How I have discovered the security flaws in Prestashop Module - Send to a Friend
One customer reported that the in-box for isPrestashop store email was containing hundreds of bounced emails, with spam, so I requested him to forward one of that emails to me.
Just by open it, was obvious that the email was originated from is store, by the native Send to a Friend module. This module is installed, by default, on the original Prestashop theme and in many other third part themes.
Example of spam message in the field name, from a real bounced back email:
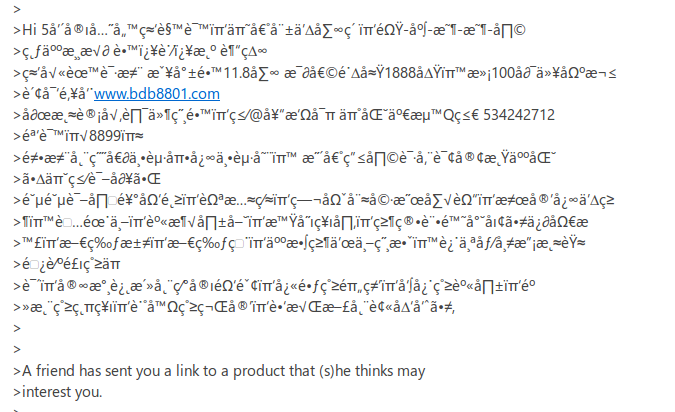
The first reaction was to reset the password for that email, but emails where still being sent from his store, as I was able to check in the server logs.
Second reaction was to uninstall the module, but the log in server was still indicating emails being sent almost every second… wait what is going on here???
First Security Vulnerability - Emails can be sent when module Send to a Friend is not installed or disabled
Looking into the module code, that handles the Ajax call for the Send to a Friend Form, located in the product page of any Prestashop store, I immediately noticed that the code is not performing any check to see if the module is active or not.
So I quickly applied the following hot fix to modules/sendtoafriend/sendtoafriend_ajax.php:
// Old line of code
if (Tools::getValue('action') == 'sendToMyFriend' && Tools::getValue('secure_key') == $module->secure_key)
// new line of code checking that the module is active
if ($module->active && Tools::getValue('action') == 'sendToMyFriend' && Tools::getValue('secure_key') == $module->secure_key)Second Security Vulnerability - Spam injected in each email sent from Send to a Friend module
Now that the module only works when active is time to check how the spammer was able to inject is content into the email.
A quick look into the email received from the Send to a Friend module allowed me to see that the injected content is in the place where the name of the friend, that will receive the email, should be.
Time to another look into the code and I can see that the field name and email do not have proper validation and sanitization.
This one is more time consuming and tricky to solve in order to not allow spam in the field name, therefore no hot fix was applied and the module was remaining disabled.
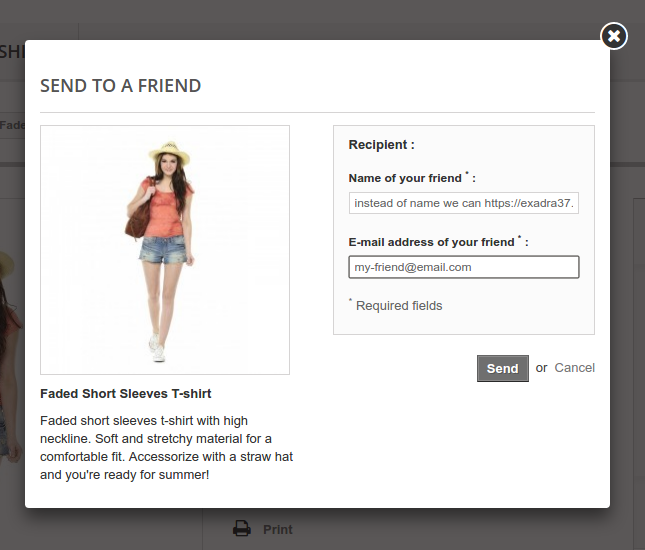
Example of sending an email to a friend, from product page, with a spam message in the field name
The following screen shots have been take from a fresh Prestashop store, installed to debug this spam issues.
Filling the form:
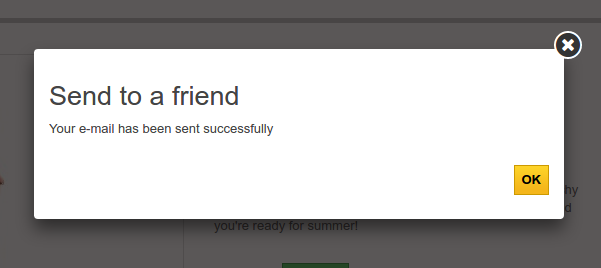
Sending the email:
The friend will receive an email with a spam message in place of his name, as you can see in outline orange part:

Reporting to Prestashop the Security Flaws
This part was harder then I expected, once Prestashop was not having any public information on is site, forum, Github or in issues tracker about how to proceed with a Responsible Disclosure.
I said was, because after my complain about this lack of info, they have now in the README a section with instructions how to proceed with a Responsible Disclosure.
Partial screen shot of README file, with info about how to proceed to report a security issue:
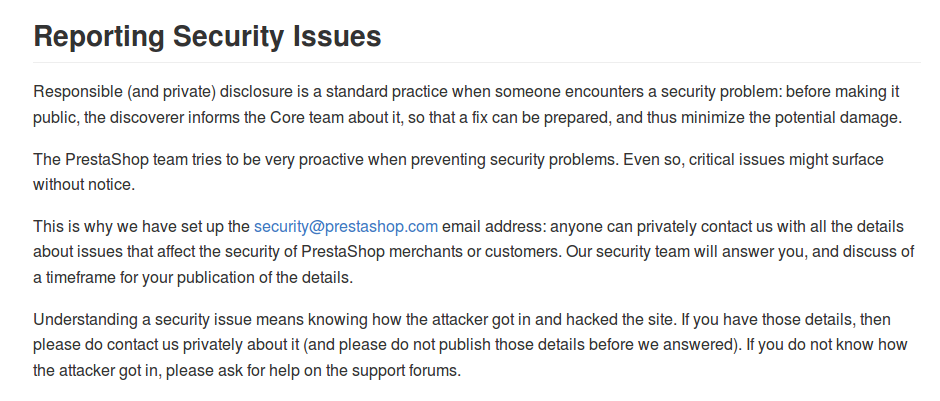
I was contacted by Prestashop in less than 24 hours after they became aware that I was trying to do a Responsible Disclosure regarding some security issues on their e-commerce platform. So my congratulations to them for the quick reply and for how they have conducted the process.
Collaborating with Prestashop in the solution for the Security Flaws
The description of the security flaws and my solution to them are hosted in my Gitlab Account, where a fork of the native Prestashop Module Send to a Friend is hosted. This fork was maintained private during all the Responsible Disclosure period and was made public only after the public announcement for the new 1.9.0 version of the module.
The Solution
After some tests conducted by Prestashop Core Developers to validate the security flaws, they have come back to me confirming that they are able to reproduce them and that my solution was accepted.
So was only time to work on some small fixes to comply with Prestashop Code Standards, as per recommendation of Rémi Gaillard, that I promptly accepted and fixed.
Pull Request
Now the only remain action is to make the Pull Request in Github so that all Prestashop users can update the module in their Back Office, just by clicking in the update button.
We want the time between making this Security issues public and the the update be available in the Back Office, of any Prestashop store, to remain as less as possible.
Therefore I need to wait for authorization from Rémi Gaillard, to only make the Pull Request on Github when he is available to merge it immediately.
This measure will prevent Spammers that became aware of this vulnerabilities, through the new release in Github, to not have a big window of time to explore them.
Prestashop Stores Owners
Do not loose any time and click in the update button in your Back Office as fast as you became aware of this or you see that your module needs an update.
Remember that the best defences against security vulnerabilities is to maintain all your software up to date. This is true for any kind of software, so don’t be lazy and update them frequently.
Links for Send to a Friend Module
Disclaimer: What I expressed here is only in my behalf and doesn't represent the company I work for, or any previous one, neither my family, friends, colleagues or anyone else unless I explicitly say so.
Comments
Disqus is disabled on my Blog because I don't agree with their policies.